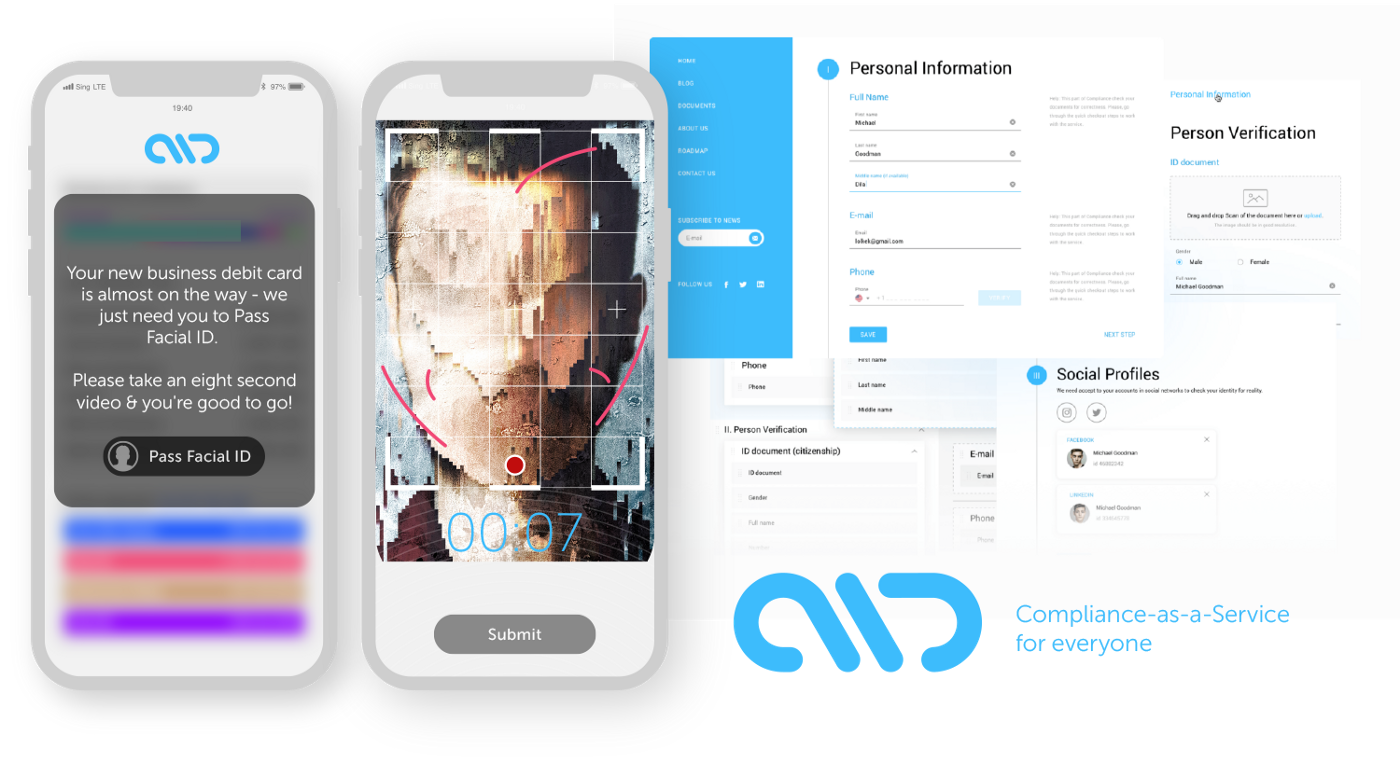
Compliance is sexy, and Arival knows it
How we created the coolest compliance ever
When we decided to create a bank for crypto-related clients, we were obviously aware that the regulator’s main concerns would revolve around compliance. We wanted to ensure we could answer the questions surrounding how we check our clients, onboard them, why our bank won’t be used for money laundering, and other criminal activities. When you acquire a bank or apply for a license, this very element of compliance is really what keeps the regulators’ blood flowing. In case your clients fall under the ‘higher-risk’ category, we also must go to bed thinking about compliance and wake up to the very same thought.
Our initial pitch for the regulator was the following: we researched how these clients (crypto-exchanges, crypto-wallets, crypto-funds, ICO-backed startups) verify their customers — rating 0, 1 or 2 on a 5-point scale — and then analyzed different bank approaches to this process — 4 or 5 for good banks. Our “offer” was to start from a point of 3 (yes, this is not 4 or 5, but better than 0, 1 or 2), making the market more transparent, and then gradually upgrade to a 4 and 5 rating.
The regulator had other plans for us — “No chance we will let a 3 or 4 rating fly, you have to be a 6 on a five-point scale if you want to work with these type of clients. So surprise us.” That’s exactly when we put the matter in our own hands by engaging our partners (one of the most reputable compliance firms in the world — Promontory Group, an IBM company and the famous DLA Piper legal team) followed by inspiration (and the vision/thoughts) of our friend David Birch (the author of a best-selling Identity Is The New Money, and a renowned compliance, fintech, blockchain and where-it’s-all-headed expert).
A.ID: FOLLOW THE MONEY
A.ID — that’s how we named our internal project, aimed at the creation of the best compliance for banks and their clients: a convenient and simple solution for customers providing integrity and complete transparency for the regulator.
When you meet a banker and say ‘compliance’, by his facial expression you will understand that it is synonymous to an ‘evil you’re forced to tolerate’ (like how kids think about school) and another ‘tedious burden.’ In our case, we have understood that if we want to create the best compliance ever, not only do we have to aim at a 5 (or 6!) with our ‘homework,’ but genuinely love our compliance with all of our hearts. So, this is our lovestory. Let’s go through it step by step — what we do and how we do it, what we check and what makes us different from the others.
“Follow the money” is a catchphrase popularized by the 1976 drama-documentary motion picture All The President’s Men, which suggests a money trail or corruption scheme within high (often political) office. Origin: For the film, screenwriter William Goldman attributed the phrase to Deep Throat, the informant who took part in revealing the Watergate scandal. However, the phrase is mentioned neither in the non-fiction book that preceded the film, nor in any documentation of the scandal. The book does contain the phrase “The key was the secret campaign cash, and it should all be traced,” which Woodward says to Senator Sam Ervin. This may have been condensed to the phrase “follow the money” in the screenwriting process. The phrase Follow the money was mentioned by Henry E. Peterson at the 1974 Senate Judiciary Committee hearings as Earl J. Silbert was nominated to U.S. Attorney. A 1975 book by Clive Borrell and Brian Cashinella, Crime in Britain Today, also uses the phrase. Since the 1970s, “follow the money” has been used several times in investigative journalism and political debate. One example is Follow the Money, a series of CBS reports. In the 2002 episode “Game Day” (number 9 of the first season) of The Wire, Detective Lester Freamon uses the phrase when investigating the dealings of a Baltimore criminal gang to explain the political difficulty of investigating organized crime, saying “You follow drugs, you get drug addicts and drug dealers. But you start to follow the money, and you don’t know where the fuck it’s gonna take you”. In September 2016, the Trump campaign used the phrase in criticizing Hillary Clinton and the Clinton Foundation. In February 2017, Carl Bernstein used the phrase to encourage reporters to discover President Trump’s potential conflicts of interest.
Why weren’t we satisfied with similar solutions and other startups?
To make it clear, we started by looking for a perfectly ready solution to partner up with. We didn’t succeed for a number of reasons:
- Some do KYC, very few do KYB (know-your-business);
- Most solutions are focused on onboarding, yet very few do onboarding and ongoing compliance at the same time;
- Few companies are really good at what they do, but each of them focuses on one element: screening blacklists or other databases, transaction fraud-monitoring or the verification/analysis of documents, photos, & videos;
- Some focus on a specific jurisdiction and start lagging behind other international clients, that might have fragmented ownership structure;
- Some boast having Uber and Airbnb among their clients, but not a single bank; while the presence of a bank as a client is the market’s ultimate Sky High, trusted by regulators more than anything else.
Eventually, we came up with a solution in a form of an “automated” client journey. We designed the logic ourselves. On each step within the journey, we decided add in one (or several) custom providers focused on the respective step, process, procedure, or type of data.
Below is the detailed description of several blocks our compliance consisting of — CDD, EDD (KYC&KYB), and Ongoing compliance. (Other blocks — Segmentation of clients, Risk profiles, Internal controls, Clients offboarding, Monitoring&Reporting, Education&Assessment, Audit, — aren’t visible to clients and are of course related to the bank’s internal processes.)

CDD (CUSTOMER DUE DILLIGENCE)
· KYC (KNOW YOUR CUSTOMER)
To make it clear — our bank works with businesses. The majority of banks that work with companies check them purely just as companies. As for us, we believe that any company is a group of people, its ultimate beneficiaries, including employees and others managing it. When someone signs up or logs into their bank account — it is never a company who does this, but a specific person, and we always need to know who it is to devise a mutual trust.

oAuth / user account registration — creation of login and password for a specific user. Architecture of a user account is created according to the ‘Personality + set of roles’ logic. What does this mean? Let’s say, you are an owner or an employee at several companies, serviced by Arival Bank. You will have a basic individual account with your name, with your roles ‘CEO of company №1’, ‘Employee of company №2’ or ‘shareholder of company №3’ tied to it. The system constantly checks the entire database for similar accounts in order to avoid double accounts or fraud. All other banks create a new entity for the types of relations, which resembles a schizophrenia (excuse me) and gets in the way of true compliance, which will be more efficient if you possess more data on a client in a singular account and database.
When you sign up and later log into the system each time, your IP-address and MAC-address of your device are scanned automatically to understand the geography of your internet access and the type of device you log in from. A plethora of correlations is being checked here:
-whether the user uses a single device for log in or suddenly a new device comes up, how often they change devices, etc;
-whether a user logs in from an unexpected country (including countries under sanctions) compared to his previous behavior;
-whether the country of internet access matches the place of your citizenship or residence. Time zone is being defined and ‘traditional’ log in hours are filled in automatically. The solution is created the way that if an unusual situation happens, you are not blocked, but asked questions — if you have travelled abroad for a holiday or a work trip, lost your laptop or acquired a new one, woke up in the middle of the night and decided to work, or literally anything else, you will be understood and your behavioral pattern will be remembered. If suspicion arises that somebody answers the questions for you, a video call can be initiated. We transparently show all data about each system log-in and log-out to the user — you can chose the settings yourself: whether you add your IP and MAC-address to the ‘trusted’ list or it was a one-time log in.
-Mobile number and e-mail verification — you receive a code to verify that it belongs to you. Seems pretty traditional — but we have two differences. First — from the start we assume that you might have several phone numbers, e-mails and even physical addresses. This is absolutely normal in the modern world. If one of your sim cards was stolen or roaming doesn’t work, but you have provided other trusted numbers in advance, there will be no difficulties. Second — for instance, we not only confirm that your phone number exists, but check what provider and country it belongs to (matches your country of citizenship, residence or internet access). We also aggregate metadata on how frequently this provider is used for fraud (you can choose a mobile service provider in the system and see how many clients use its services).
-Passport and ID verification. First, we provide you with an opportunity to upload more than one document: your passport from country of citizenship (some countries provide two valid passports at the same time), confirmation of your residence in another country (even if you are on a long business trip or touristic journey). This is crucial — the world becomes more and more ‘horizontal,’ people constantly move, and it is simply stupid to tie a person to one single country. Second, we automatically take a note on the expiration date of each document — the system will remind you (and itself) to renew your document (a simple thing, but offered only by few). Third, we check documents for any alterations or other intervention. And finally, we check databases on negative or criminal records about you.
-Confirmation of residence address. The same works here — you can have multiple addresses in different countries. This is usual. You can confirm your addresses traditionally — by providing utility bills or a bank account statement, — as well as asking us to send you a physical letter with a unique code (you can pick it up upon the presentation of a passport only). All addresses are checked with Google Maps and other online maps instantly, and are checked for public information about these places (what else is present there, the type of building etc.).
-Bank card verification. We are hardly the first bank in your life. We work with companies — and we like to meet our clients in person at the moment. So we believe it’s weird if you have no bank card at all. You provide its data (we don’t store it) — we check its type (gift-cards don’t work, classic debit or credit cards are welcome), whether it is active or not (we charge a small sum and return it instantly, remember its expiration date (to ask you to update this information), and attentively examine the card’s issuing bank. The same works for bank account statements. We store them separately and analyze which banks have already verified you before us, their country and reputation.

-We ask you to log in with your social network accounts, Facebook and/or LinkedIn. We are oriented on business clients from the technology sector who run their business online, and we will assume it suspicious if you there is zero information about you on the internet. Knowledge of your social network account (if you decide to share it with us — you can choose not to trust us and not share the information on each step): comparison of your name and last name, e-mail and profile picture with the ones you provided will be very helpful for us. At the same time, your decision to share your social connections information (friends, colleagues, family) will be taken very positively from our side, as we highly value your trust.
It’s looking more like an episode from Black Mirror. Yes, we are even afraid of it… So I hope we are not developing this :)
-Fill in type the of employment and average level of income. You can put checks in relevant boxes if you wish to tell us more about you (or not). What you should understand here is that the higher transaction amounts you expect with your account, the more interested we become in who you are and what you do for living (I think you understand why, don’t you?).
-Next step is recording a short video with you — as we don’t see each other face to face, we need to know that your data wasn’t stolen by a malicious user. We compare your video with photos from documents (and social networks, including YouTube).
-Next, you sign (electronically on your device screen or take a picture of your live signature) your approval for A.ID to collect, store and analyze this information (until you change your mind and ask us to delete it), pass it to Arival Bank and other partner services of the bank (only with your separate consent). Then, your application for the bank account opening is created.

· KYB (KNOW YOUR BUSINESS)
In the previous phase, your personal account was created. Now, it’s time to create your first role: your relation to the company, for which you open an account in our bank. You need to specify your position in the company(shareholder, director, employee or outsource accountant) and confirm that you are authorized to open an account for it.
-You fill in the company data: name in the system, DBA name, legal name, country, date and number of registration. You choose what industry you’re in or the several industries you may belong to. Website, LinkedIn, Facebook or Github page — if you have it. Company Address of course. We then check if there has been any negative or criminal information about your company.
-You fill in an approximate number of employees in your company, estimated turnover and countries where you plan to receive/send money most frequently.
-Provide ownership structure information — what percent of shares belongs to whom: you just state the percent, person’s name or holding company name, and contact e-mail (beneficiaries will have to pass verification themselves — we will send them notification and link separately). Also, we will need your CEO’s (and other top managers) contact e-mail.

EDD (ENHANCED DUE DILLIGENCE)
· In special cases, we can ask you to fill in all employees — and ask them to pass verification themselves. For example: one of the most common ICO-related frauds includes 3–5 people making a gorgeous presentation where they put pictures on non-existing or unaware ‘employees,’ raise money and disappear. In this case, we might want to make sure that apart from the owners (and their big plans) there are other employees in the companies, competent and capable of bringing these plans to life. The same works for ICO advisors and mentors — if you use their names in public materials and they ‘guarantee’ your credibility with their names, we would like to know more about them.
· From the point of beneficial ownership compliance rules, the regulator is obliged to disclose information about all shareholders with a 25% and higher stake. Or in the case of work with high-risk clients — from 10% and higher. Our system is designed as following: encountering each new “company as a shareholder” entity, it “loops” and “knocks inward” to disclose every shareholder with any number of shares — until only real people are left. It’s important to understand two things here. First — the user who fills in the registration form doesn’t have to provide all data himself — only contact e-mail of a shareholder for the system to contact and ask them to share more info on themselves. Each new participant has to tell us about him or herself personally and nobody can do it for him — because it is very important for us to know who exactly sits in from of the screen of the other side, how transparent and sincere he or she is with us, and whether we can trust them. The second important point is that we rely on the inviolable value of ‘presumption of innocence’ — the client doesn’t have to convince us he or she is not a fraudster. Yes, they have to be open, but we initially assume he or she is a law-abiding citizen or company. That’s why your account is opened as soon as you fill in the minimal data about yourself and your company — and we have found nothing negative based on the basic information. If the company has a complex ownership structure, or something needs clarification or additional information, the system places limits on account usage (but it is opened and becomes active at once), and raises these limits or eliminates them as new information is provided. In case of intentional concealment of the information or inconsistency of received answers — open account will be blocked.
· If your business needs a special license in your country, we will ask you to provide it as well.
· For better understanding of your business we might request additional materials, if you have them: whitepaper, business plan, product or business presentation, legal opinion, team presentation, investment deck. We don’t ask you to create anything new just for us — we simply ask you to share what you already have. Our team has over six years of experience in investment analysis and due diligence in fintech — and an understanding what we should pay attention to.

If you intend to operate big amounts of money through your accounts, we might ask you additional questions on your source of funds and source of wealth. For example, you have conducted an ICO — so you hopefully have already checked your investors and token holders. If the previous verification doesn’t comply with our standards, we might ask you to upload existing information in A.ID, and double request (and double check) the missing information. You don’t need to collect or process data manually — the system will automatically fill in the boxes with existing information and send the links to participants for them to add more information about themselves. Or if you are a crypto exchange, which means you handle money of third-party people, it is crucial for us that you verify them. The same process is applicable here — if the level and amount of verification seems insufficient to us, we might suggest that you use A.ID to raise the verification level and information amount.

ONGOING COMPLIANCE
· According to statistics, real big fraudsters don’t get caught on the stages of registration or onboarding — considering they have learnt to bend the rules. Transactions make it possible to track and catch them. That’s why the ongoing compliance module is crucial for us.
· Based on the information we receive about the company, we will decide whether your business really exists, as well as ‘tag’ your estimated expenses and items of expenditure in the future. In case your company has frequent or abnormal transaction sizes, the system will rely on these tags (or flags) to decide whether this information complies with the information you have stated about yourself during onboarding (countries of consignment and destination, purpose and frequency of payment etc.).
· Back to the accounts, KYC & KYB — we treat our ‘clients’ (and create accounts accordingly) as not only our clients, but everybody, who somehow encounters our bank during transactions. When being hired, our potential employee undergoes the same verification process and uses the same login and password for his/her work computer. If he/she also decides to become our client (we hope so, lol) — a new role will be added to his/her account. When 1) somebody sends money to our client, 2) receives transfers from our client or 3) if he/she is a shareholder or a counterparty related to our client or 4) friends and colleagues from social networks — as soon as the system sees a new entity, it creates a new box and fills it with new data, one piece at a time. Thus, our clients have active accounts, and other parties — passive accounts. If any of these counterparties also decide to become our clients, the verification and onboarding procedure will be easier for both of us, as we already know them, have basic data, and the trust was already existing. When a box is created, the system automatically tracks activities related to him. For example, our 10 separate clients have sent money to an outer company — the trigger works, and the system automatically starts to search for additional (public) information about the counterparty. If information is unavailable or negative, it automatically sends the money recipient a notification to pass an additional verification with us. The same works for money senders.
· Our system is built on the principle of constant data triangulation: 1) what we know about the company in general (original data base), 2) who operates in its name and what he does exactly (country, device, time, type and frequency of actions), 3) social and economic connections around the company and the person behind the screen (friends and colleagues from social media, money senders and recipients from other banks, shareholders, management and employees of the company). Real professional fraudsters have long learned to bend banks’ verification systems, providing suitable answers, clean shell companies and reasonable transaction goals — thus, it is much more efficient to track them implicitly, on the meta data level: general non-obvious social connections, similar behavioral patterns among non-related clients, etc.
Thank God we are not doing this in China!:)
MAGIC
· As you know, Arival Bank isn’t developing and doesn’t plan to develop most of its own products. On the contrary, on every vertical paradigm we find an awesome fintech-startup who has already mastered a specific product or service. It doesn’t make sense for us to re-invent the wheel, so we integrate with these startups (this approach is exactly what we call the ‘first fintech-bank creation’). We have highlighted 12 key verticals for ourselves and future customers. After winning Finovate, we have received an enormous number of applications from other fintech-startups that don’t fit into our primary focus, but can be potentially useful to our clients. To make sure our client doesn’t need to register in each of these fintech services, create an account and provide the same documents, we will need to unite our compliance requirements and user account system with these services.

· This is why we have created A.ID as a separate solution with an open API. It means that you provide data and rights to process and check it to A.ID — our bank and other partner services request the permission to process this data and results of its verification (with your permission — which you can refuse), and use the same username and password “log in with A.ID.” It gives you the opportunity to save your time (and nerves) on registration and each new log in. And these are additional trust reasons for compliance. Only fraudsters lose here — in case of fraud in one of the services, you are going to be blocked in all other partner services.

COMPLIANCE MANAGER’S DESKTOP
· A.ID treats Arival Bank’s (and its partner services) compliance managers as clients and aims at creating additional value for them. Firstly, before their work with A.ID starts, the compliance manager himself and his company has to pass the same verification process in the system as its future clients.
· Next — you launch the “Constructor” module, where you need to create types of clients (if your clients fall under different categories), fields you want to check, their order, depth of checks in each step, system’s reaction on blank required fields or negative information (yellow or red flags). If you want to create new fields — you are welcome to do this in the same window. Let’s go!

· You have received a code you need to paste on your website or mobile app. Arival Bank has already become the first client of its own solution.
· Now the client sees a “Log in with A.ID” button on your website — if he has already passed the verification elsewhere, he simply logs in as an existing user of A.ID, if not, the registration procedure starts.
· As a compliance manager, you see the key metrics on the dashboard: how many clients have started the registration process, how many of them passed it, the clients you have approved and rejected. You can see the yellow and red flags and ask additional questions.

WHY WE ARE DIFFERENT
· All the paragraphs above in italic describe the features that no (or almost no one) existing players from different market implement. Nobody does this in a comprehensive manner. If you know somebody who does all of the mentioned above — let us know! We will close this branch of the bank and become clients of this solution.
· We understand that we aggregate a lot of client data — to work with high-risk clients we need to trust them, and to be able to do this we need to see that the company and its representative are open to dialogue with us. But we understand, that this amount of your personal data is a very sensitive question. That’s why we create a separate interface for users — you can always see what information about yourself you provided to us and when, who else requested it (with your permission or refusal), what details, whether he stores it or not — and make an automatic request to have it deleted. In this sense, we are loyal advocates of our clients. Yes, your trust and openness is fundamentally important for us, but we follow our standards ourselves — we are going to show you what we know about you and how we use this information, and if you lose your trust in us, we will show you that we have deleted it.
WHAT’S NEXT?
What is already done:
- Everything related to compliance is designed as a separate solution and integrated with our bank via open API
- Personal account where the bank itself and its big clients will be able to set up required verification fields, see and track statuses of the verification process
- Fields and interfaces for personal and business data collection during onboarding
- For now, we are integrated with one provider (a great one, but the only one so far) for blacklist checking.
- Inner policies and regulations: Cores System Task Analysis; BSA/AML Risk Assessment; OFAC Risk Assessment; AML Risk Model; Account Monitoring, Investigations and SARs; CDD/EDD/KYC module; Vendor Management; PDSA (Plan, Do, Study, Act) Cycle; Cybersecurity; Reputation Risk Management.
What we are working on:
- We want to add more and more third-party verification services to each step of our onboarding process — there are lots of databases in the world, old and new, that check different parameters, new startups and technologies emerge that take a single verification step and take it to the new level;
- At the moment, we are focused on new clients’ onboarding — we need to spend more effort on ongoing compliance, what the clients do after they have already become our clients and started to make transactions;
- We want to make setting of risk-profiles not constant, like they are now, but dynamic — to make it possible to create new scripts for different participants;
- Interfaces for compliance managers require further elaboration — not only to clearly see the triggers during onboarding (like now), but also to be able to react to these flags instantly during transactions, ask clients additional questions and analyze the answers at once;
- When there is more data, we want to integrate a neural network and artificial intelligence. At the moment our system works on our own questions and answers — the good analogy is “What is a cat? It is a small fluffy animal with four paws and a tail.” But this approach excludes bald cats, or cats without a tail or a paw. Machine learning enable neural network to show one or two hundred cats at once, and the machine itself determines what a cat is. More than that, it constantly adapts its answer on the basis of the new data. And then, it learns to ask the questions itself, to group it automatically and to create new risk profiles.
- We would like to help our clients not only technology-wise but also with:
-Analyzing and upgrading existing compliance policies and specialists, outsourced to manage this process;
-Doing our own higher-quality audit of their compliance, as well as provide services for regular training and skills development.

Why we believe that we do the right thing: the core-banking system, that our bank functions on, offered to scale our product and rent it to other banks working on the same system, when they saw what we build for internal use. This is super cool — if big international banks think that what we do and how we do it is more convenient for the client, more reliable in terms of verification and cheaper, it is a fantastic opportunity for us to test & perfect our system based on the experience of our bank and other banks as well.






